Have you ever considered how much your mobile device is like a magic wand? Think about it. You use your mobile device regularly to conjure solutions to a variety of problems — big and small — that befuddle you. Also, you can pull your device from a pocket or cloak (should you don that attire) within seconds to remedy the situation. A quick incantation (or opening of an app) solves a problem for you or improves your life, even in the slightest way.
True, your mobile phone won’t save you from Voldemort or a Death Eater (Harry Potter is on the mind thanks to summer reading lists!), but it’s still powerful. Designed for ease of use, it allows you to quickly and conveniently complete tasks and gather the information you need throughout your day.
The key difference is that a wand is actually magical, while your phone is like magic. This article is all about understanding the magic behind some of your mobile device’s most misunderstood usages with regard to geolocation, data integrity, and enterprise mobility management.
Geolocation
Geolocation is the process of locating a device using GPS, Wi-Fi tower triangulation, or cellular triangulation.
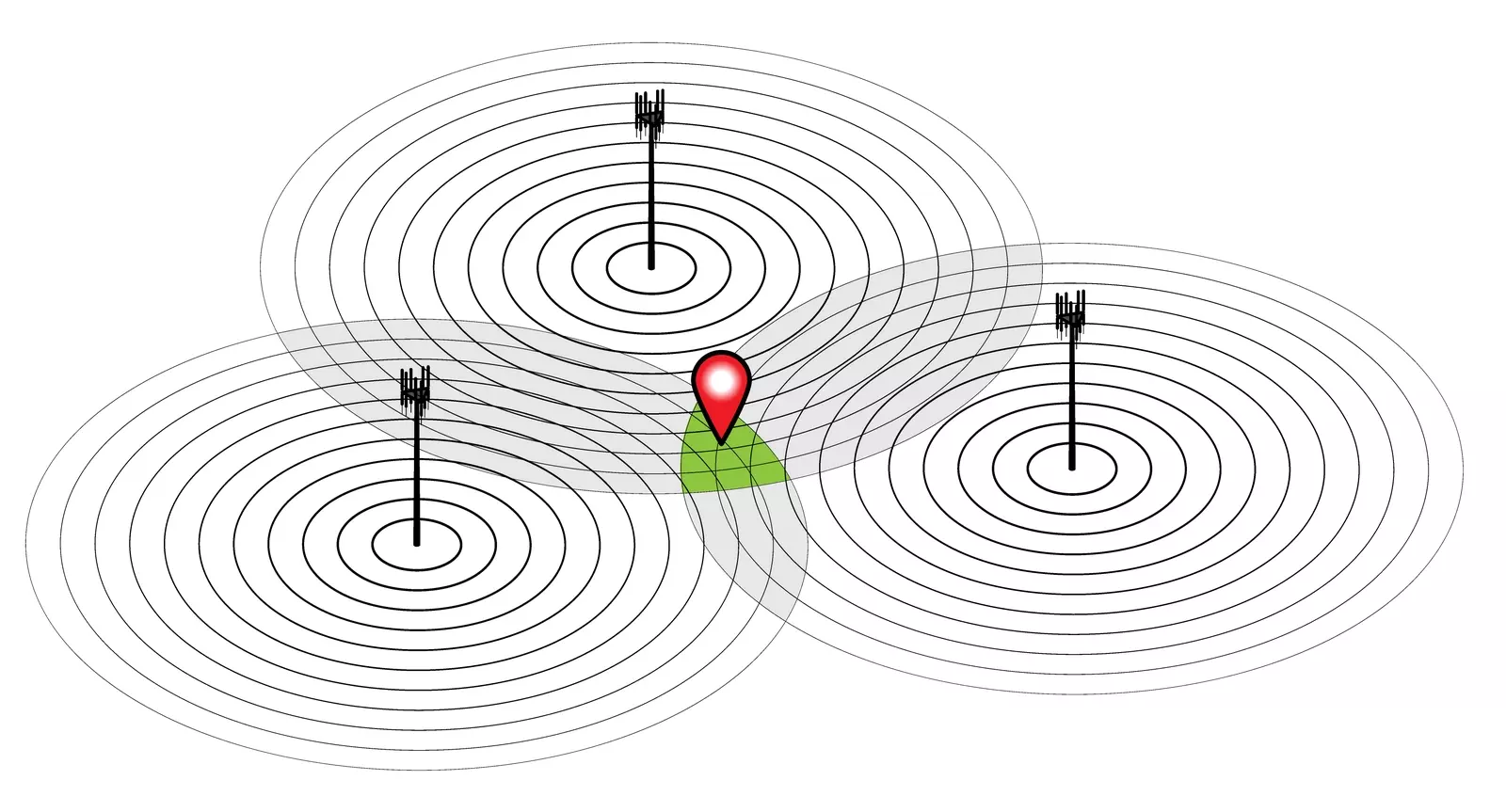
Geolocation is often employed by businesses to share promotional information with you based on your mobile device’s location. Geolocation is used in your Kronos® solution to present information that is pertinent to users based on their location.
Consider Lily, a store manager, for example. Lily oversees multiple retail outlets from Portland, Oregon, to Seattle, Washington. Geolocation enables her to have visibility into the data that’s relevant to the location she’s visiting at the time. She’ll see the information from her Kronos solution for only the Tacoma store, including her employees, when she’s at that location. She’ll have the same kind of experience at the downtown Seattle site. In other words, geolocation capabilities make Lily’s job easier by displaying and filtering the information she needs to do her job effectively based on her location. The best part is that she doesn’t have to change any settings on her phone to make it happen! Pretty cool, right?
But how exactly does it work?
The geolocation functionality of the mobile applications for the Workforce Dimensions™ suite from Kronos and Workforce Central® requires defining and creating known places. A known place is a circular geographic area based upon a GPS location point and a radius. The location point is determined using a set of longitude and latitude coordinates. Additionally, the radius meters establish the boundary around the location point. These three data points — longitude, latitude, and radius — establish the criteria for a designated known place.
Known place = longitude + latitude + radius
Here are some examples to help you visualize:
- Compass. Think of it as an old-fashioned compass. Half of the compass has a sharp end to place on the paper that becomes the center, while the other end (usually with a pencil inserted) draws the perimeter to create an almost perfect circle.
- Or tetherball! Reminisce about that sturdy old tetherball court from your school or town playground. The pole is the location point, and a full circle of the volleyball on a rope around the pole represents the circumference of the known place.
Once your organization has created a known place, the next step is to assign it to your users. This critical step is what enables Lily, our manager, access to the data that’s relevant to the store she’s visiting.
A quick recap. Geolocation is the process of determining the location of an electronic device like your mobile phone. A known place is the Kronos term for the creation of a defined and specific geolocation.
Geosensing and Geofencing
The next magical mystery we’re going to explore is using geolocation with your Workforce Central or Workforce Dimensions mobile application. There are two ways — geosensing and geofencing.
Geosensing is when your device is recognized within the known place. It’s also what allows Kronos solutions to present only the data relevant to that location to your managers who are associated with that known place. In other words, geosensing is using geographical inputs like latitude and longitude to sense the location of a mobile device. It’s very similar to how Google Maps and Waze know your location when you have your phone with you.
Geofencing also uses known places, but the concept here is more about establishing an enclosed area — not all that different from the fences in our school playgrounds and backyards. Let’s be honest; the purpose of a fence is to keep what you want within a particular space without letting in what you want to keep out.

Geofencing is intended to promote and acknowledge when an employee punch is within the respective perimeter. More simply, the geofence is used to determine if the employee is at work when punching in or out. Geolocation and establishing known places offer your organization a significant amount of flexibility with regard to operationalizing location status and preferences. For example, you can limit job transfers and punch transactions that are outside the radius of the known place, meaning that the employee’s mobile device is beyond the fenced-in area that would allow certain behaviors to be accepted. Similarly, you can allow punches outside the designated fence and add a notation that the punch was captured outside the radius.
And just how do we ensure that punches coming in through the mobile app are secure and valid? Well, that takes us to our next misunderstood mobile item.
Punch data validation
Because even magic can’t vanquish the various evil spirits that lurk about, defenses are applied to the back end of the mobile application to ensure the security of accurate punch data. In this section, we’ll focus on data integrity as it pertains to employers and organizations that follow a bring-your-own-device (BYOD) approach.
Simply put, BYOD refers to when employees use their personal devices to access their organizations’ instance of the Workforce Central or Workforce Dimensions mobile app. Two of the most common questions that customers ask are how valid is the data that’s submitted from an employee’s device and how do we protect the authenticity of the data that is provided? As a leader in the human capital and workforce management industry, Kronos takes the accuracy and validity of employee data very seriously. It’s the backbone of what we do, so it’s with great emphasis that I say Kronos is committed to ensuring data integrity to the best of our ability. Multiple efforts are taken to protect and safeguard your data.
Here are three ways we approach mobile data validity.
- Blocking access: First, access to the solution is blocked if the mobile device is compromised. More specifically, if the Workforce Central or Workforce Dimensions solution detects that the mobile device has been rooted or jailbroken, location and other features will be disabled and no longer available. Jailbreaking a phone means that someone has gained full access to the root of the device’s operating system, including access to all features. In a similar vein, rooting is the term for the process of removing the limitations on a mobile device.
- Checking data: Next, the mobile app is designed to prevent data manipulation by ensuring that the key data points such as time and GPS have not been compromised. These efforts include validating time with external (to the device) systems, using mobile operating system checks to ensure data protection, and programmatically confirming that the location data is sound. If these efforts fail and data is suspect, the data will be marked as such.
- Adding notes: Finally, if all prior measures have been taken but there’s enough evidence of foul play, the Workforce Central and Workforce Dimensions solutions take notice and add a note to the punch in the timecard. This action is taken to alert your organization that the data might be dubious and is carried out if:
- Location data is required but is not available
- Pattern analysis draws location data validity into question
- There is suspicion the time associated with a punch is incorrect
Even with data validity measures in place, it is important to note that the lack of device ownership limits the extent of what can be done. Organizations need to weigh the benefits of BYOD against the risk of data corruption. And speaking of risk, this makes a tidy transition to learning more about some of the ways that you can reduce the risk when your organization has a BYOD policy.
Enterprise mobility management
Let’s start with some background on enterprise mobility management (EMM). which can be summed up with one word — evolution.
Perhaps I should elaborate. Times are changing, and the evolution of mobile phones from cellular flip phones to minicomputers paved the way for employees to use their personal devices in the workplace — whether for checking work email, the schedule, or any number of work-related tasks. As we already learned, there is risk involved when employees use their own devices to access their employer’s data. EMM providers emerged out of necessity and an abundance of caution to protect employee data, organizational data, and any other information that should remain confidential.
Enterprise mobility management (noun) = an approach to securing corporate data integrity in a workplace that is becoming increasingly wireless through smartphone and tablet usage. Learn more on page 21 of this guide.
Today’s EMM providers offer a range of services — the most common include device management, app management, and additional security measures like password and identity protection, encryption, and more.
Before we move on, it’s important to understand the difference between Kronos mobile apps and EMM application providers. Kronos mobile apps, regardless of product (Workforce Dimensions, Workforce Central, etc.), should not be thought of as EMM applications. Kronos mobile apps are designed to allow EMM applications to manage them. Organizations that leverage an EMM provider can do so knowing that their Kronos mobile app supports the EMM applications with app distribution, the ability to require the presence of a secure virtual private network before a user can access the system, and the ability to prepopulate a URL for all mobile users in the network.
Did you know? One of the most frequently searched questions on kronos.com and Kronos Community comes from employees unable to find their organization’s URL to access their organization’s instance of the mobile app. Learn more here >
Let’s focus on app management, one of the common services that EMM providers offer. App management refers to an organization’s ability to manage mobile applications on employees’ devices. App management can range from updating mobile apps to URL propagation to applying security policies to the app and more. Then, understanding the ability to control access with dynamic mobile profiles is equally compelling because it enables an organization to specify access to the mobile app depending on which device the employee is using.
I’m going to pause for a moment to address the elephant in the blog because I can see how you might start to consider EMM as a form of witchcraft. What kind of trickery is this? Getting access to phones!
Well, it’s a form of security. It’s a good thing! EMM is what allows an organization to mark a mobile phone as a corporately managed work device. This is one of the best ways to secure data for your employees and your organization.
Once a device is marked as managed, you can create a dynamic mobile profile that allows your employees and managers full access to the Kronos mobile app when connecting from a corporately managed device. Integration with an EMM provider also gives your organization the flexibility to specify if employees are accessing Kronos mobile apps from personal devices. If devices are personal rather than corporately managed, you can limit the level of employee access and provide certain restrictions.
Become a mobile wizard with these key resources
Now you understand why mobile devices are like magic wands and know about the top misunderstood mobile topics. To equip you with the tools you need to officially become a mobile wizard, be sure to visit the Mobile Resource Center. And don’t forget that finding your organization’s mobile login URL takes more than a wave of your magic wand. You’ll find everything you need to get your users and employees up to speed quickly in the Mobile Resource Center.
Outside source used
Carter, T. J. (January 13, 2020). Enterprise Mobility Management (EMM): What It Is, Why It’s Important & How to Do It | Process Street | Checklist, Workflow and SOP Software. Process Street. https://www.process.st/enterprise-mobility-management/.
